The rise of AI in mobile phones has fundamentally changed the risk profile. What was once a balance between productivity and convenience is now a growing vulnerability.
The Threat of AI Makes BYOD More Risky
Bring Your Own Device (BYOD) programs once promised flexibility, cost savings, and employee freedom. Employees could use the phones they owned, while organizations avoided footing the bill for every handset. But the rise of AI in mobile phones has fundamentally changed the risk profile. What was once a balance between productivity and convenience is now a growing vulnerability.
The reality for businesses is that BYOD is no longer just about convenience. BYOD is now about control, security, and survival.
Why AI Raises the Stakes for BYOD
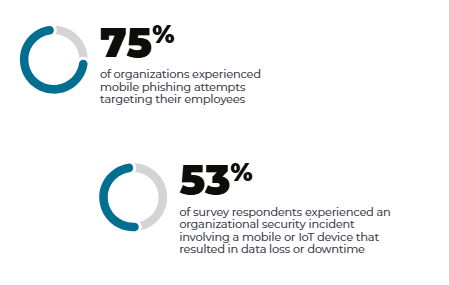
Artificial intelligence is quickly becoming part of many devices. This includes smart assistants, AI transcription, predictive text, and embedded copilots. Some apps also collect data without users knowing. On personal devices, these tools are unmanaged, unpredictable, and often invisible to IT teams.
This creates new exposures:
- Data leakage through AI apps – Employees may unknowingly feed sensitive enterprise information into consumer-grade AI tools with weak privacy protections.
- Unregulated app ecosystems – Personal devices may host AI-driven apps that bypass enterprise mobility security standards.
- Shadow usage patterns – AI can automate tasks like forwarding messages, copying files, or summarizing communications without enterprise oversight.
- Blended personal + work data – AI models may learn from both personal and enterprise activity, creating compliance headaches and data security risks.
In short, the meaning of BYOD has evolved from just being about letting employees bring their own devices. BYOD is now asking: Do we trust unmanaged AI-powered devices in our enterprise ecosystem?
The Safer Alternative: COPE Programs
Company-Owned, Personally Enabled (COPE) programs aren’t just for massive enterprises. Mid-sized organizations face the same security threats, often with leaner IT teams and fewer resources to respond. By controlling the device while still allowing personal usage, COPE strikes the right balance between enterprise mobile security and user flexibility.
Why COPE Outshines BYOD in the AI Era
- Enterprise Mobile Security by Default – Devices can be preconfigured with enterprise mobility management and mobile security solutions, ensuring policies are enforced.
- Stronger Compliance – With corporate ownership, organizations can enforce BYOD policies statistics show employees often ignore, such as restricting unapproved apps.
- Better Visibility – IT teams gain insight into app usage, data flow, and anomalies without spying on personal behavior.
- Global Mobility Support – When devices are standardized and secured, organizations can support international teams without worrying about local AI app risks.
How to Pivot Away from Risky BYOD
If your organization is still heavily invested in BYOD, you don’t need to rip and replace overnight. Instead, think of it as a staged shift toward secure enterprise mobility:
Audit Your Current Environment
- Identify how many personal devices access enterprise systems.
- Map the AI-enabled apps already in use.
- Quantify exposure with a telecom audit for mobile spend and compliance.
Establish Clear BYOD Policies
- Define acceptable use for enterprise data on personal devices.
- Communicate risks tied to AI-driven mobile apps.
- Use policy to prepare employees for an eventual COPE shift.
Adopt Enterprise Mobility Management Tools
- Leverage mobility management platforms to enforce secure configurations.
- Automate updates, patching, and remote wipe capabilities.
- Centralize visibility across your mobile fleet.
Transition to COPE Devices
- Start with high-risk groups in your organization.
- Provide company-owned devices with personal allowances to ease adoption.
- Highlight security as a benefit, not a burden.
Educate Continuously
- Share real-world examples of AI-driven breaches.
- Reinforce that secure enterprise mobility is critical for protecting both employees and the business.
- Build a culture of vigilance around mobile security.
The New BYOD North Star
People once framed BYOD policies as a sign of agility. Today, with AI integrated into nearly every app and device, they’re increasingly a sign of risk. Enterprise mobility security isn’t optional. Policies are the backbone of protecting sensitive data, ensuring compliance, and enabling true enterprise mobility without fear.
For mid-sized organizations, BYOD may seem like the easy path forward, but COPE is the overall best strategy. It balances freedom and control. In a world where AI can make phones risky, secure enterprise mobility is crucial. Increased mobility security around AI is not just a good idea, but necessary for survival.
Ready to take control of your Technology Estate?
Book a demo today and see how you can optimize your global technology management.
Calero | Technology Business Management Solutions Optimize costs, inventory, and operations for SaaS, mobility, telecom, and beyond with a single unified technology business management platform.


