In a mobile-first world, security isn’t about locking devices down. Device security is about enabling the organization to move faster, smarter, and with confidence.
Enterprise Mobility Management Solutions: Protecting Data in a Mobile-First World
Organizations rely on mobile devices for several day-to-day operational tasks. From frontline teams to executives, smartphones and tablets have become primary gateways to corporate data, cloud applications, and communication systems. That shift has created a new reality: mobility is now a core security domain, not a convenience. And without a deliberate strategy, the risks escalate quickly.
In a mobile-first world, Enterprise Mobility Management Solutions are no longer optional. They are the main support for protecting sensitive information and make sure that all devices follow security rules. This includes devices owned by the company and those owned by employees. Getting mobility security right requires clarity, discipline, and a lifecycle approach that leaves no blind spots.
Set Your Boundaries: Security and Acceptable-Use Policies
The foundation of any enterprise mobile security strategy is communication. Employees must understand exactly how to access, store, and share corporate data—especially when mobility blurs the lines between personal and professional use.
This is where many organizations stumble. Policies for COPE security (Corporate-Owned, Personally Enabled) and BYOD environments are often buried in onboarding documents or written in vague, ambiguous language. If your employees don’t know the rules, the likelihood of employees following them are slim.
A strong policy framework should clearly define:
- What data can be accessed on mobile devices
- Approved apps and required security configurations
- Restrictions on personal app installation for COPE devices
- Expectations for COPE vs BYOD usage
- What happens if a device is lost, stolen, or compromised
- Remote wipe and monitoring protocols
- Employee responsibilities for reporting suspicious activity
If your organization has no policy, there is no control. A mobile device without guidelines is a security risk waiting to happen.
Use UEM to Enforce—Not Just Document—Your Strategy
Policies only matter when they’re enforced consistently. That’s where Unified Endpoint Management (UEM) becomes essential.
A robust UEM platform gives IT teams the power to:
- Enforce encryption and MFA
- Push security patches instantly
- Control app permissions and install required software
- Lock or wipe devices remotely
- Segregate work and personal data on BYOD devices
- Monitor compliance in real time
This is the difference between intention and execution. Many organizations benefit from partnering with a managed mobility services provider—a team that handles the complexity of configuration, compliance, and ongoing administration. The mobility landscape moves fast; offloading operational burden while strengthening security is simply strategic.
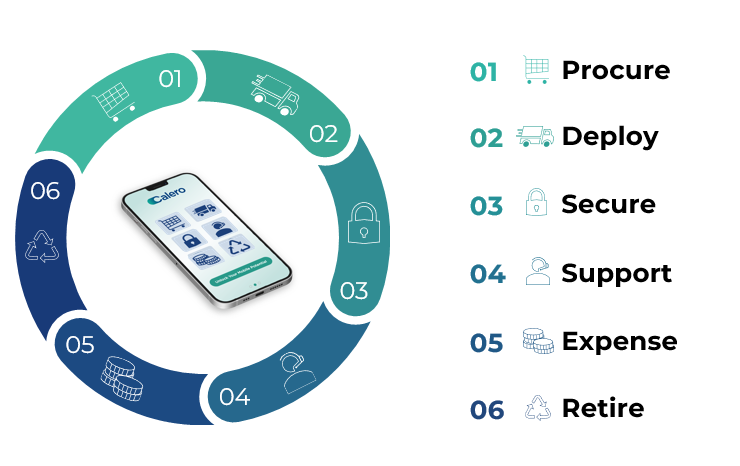
Map Security Across the Entire Mobile Lifecycle
True mobile lifecycle management is more than troubleshooting and procurement. Lifecycle management is a cradle-to-grave discipline that considers security at every stage.
Provisioning and Forward Logistics
Secure mobility begins the moment a device is powered on. The device should be configured with the proper UEM profiles, passwords, certificates, and restrictions before shipping. No workarounds, unsecured first-time logins, and no configuration left to the end user.
Reverse Logistics and Secure Decommissioning
The end of a device’s life is often the most dangerous period. Forgotten phones still contain corporate data, cached credentials, and application access. Without controlled collection, wiping, and certified disposal, abandoned devices become silent liabilities.
A secure mobility program ensures:
- Every device has a documented chain of custody
- All returns are tracked and validated
- Wiping procedures meet regulatory standards
- Recycling and destruction follow compliance guidelines
This is where Enterprise Mobility Management Solutions earn their value. A flawless lifecycle eliminates the weak points attackers exploit.
Inventory Accuracy: The Unseen Guardian of Business Mobile Security
Your organization cannot secure the device you cannot see. An accurate, centralized inventory is one of the most underrated defenses in business mobile security.
Inventory visibility ensures you know:
- Which devices are active
- Which users have access to sensitive data
- Which devices are lost, unreturned, or inactive
- Which assets require updates, patches, or retirement
- Whether COPE and BYOD programs are properly balanced
The alternative is chaos—a shadow fleet of unmanaged devices holding confidential information. No organization can afford that.
The Path Forward: A Mobile Strategy That Protects and Empowers
Mobile devices unlock productivity and accelerate decision-making. They connect global workforces in ways that were impossible a decade ago. But they also demand a modern, structured, forward-thinking security approach—one that blends technology, discipline, lifecycle rigor, and the consultative expertise of a trusted mobility partner.
In a mobile-first world, security isn’t about locking devices down. Device security is about enabling the organization to move faster, smarter, and with confidence.
Ready to take control of your Technology Estate?
Book a demo today and see how you can optimize your global technology management.
Calero | Technology Business Management Solutions Optimize costs, inventory, and operations for SaaS, mobility, telecom, and beyond with a single unified technology business management platform.